Contents
Personal Domain Considered As Work
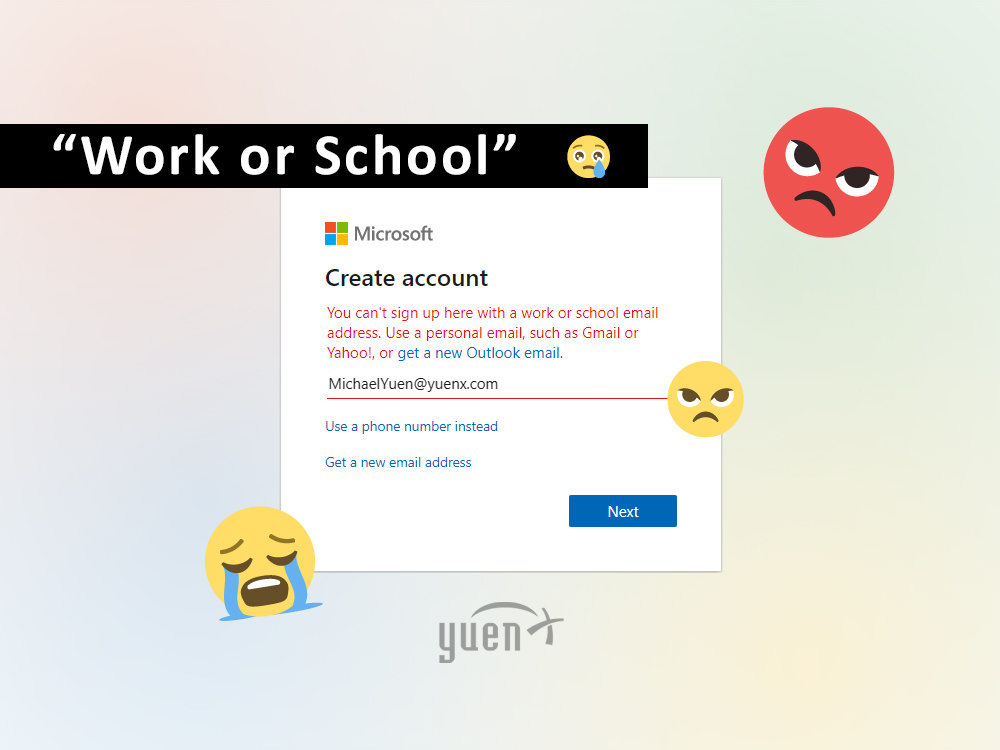
I had been running into this issue for a few years now where a domain I personally own (ie. YUENX.com) could NOT be used as the first account added to a fresh installation of Windows 10 (or 11) or be granted an Office 365 subscription. Attempting to do so would throw an ominous error message: “You can’t sign up here with a work or school email address. Use a personal email, such as Gmail or Yahoo!, or get a new Outlook email.”
“But I never associated my domain with a work or school Microsoft account,” I thought to myself. Numerous contacts to Microsoft for support went nowhere over the years. I had given up for some time and thought that the issue arose after I had previously applied a Microsoft Extended Warranty for Business towards one of my personal Microsoft Surface Pro devices. Since I had found workarounds to still allow me to use my @domain.com email addresses with Microsoft Windows and other services, it was no longer a priority to pursue.
Root Cause
Recently, I again dug some more into the long-running issue and decided to contact Microsoft Azure support. I remembered having previously signed up for an Azure trial account — somewhere between 5 to 10 years ago — to study the cloud service while I was still an IT Systems Engineer. Perhaps my domain was associated with Azure and in turn was treated as a work organization? When the support engineer could not help, I reached out to Microsoft 365 Business Support instead at (800) 936-4900 for U.S. customers.
As it turned out, my domain indeed had a Microsoft 365 tenant associated with it. We were finally getting somewhere…
My personal domain was associated with a free Microsoft 365 Business subscription.
The M365 Data Protection support person could not give me any details about the M365 tenant for privacy and security concerns, and so I had asked him to help me retrieve the Global Administrator account. A lengthy, secure recovery process ensued after which I gained access to the Microsoft 365 Admin Center via the admin@tenant.onmicrosoft.com login.
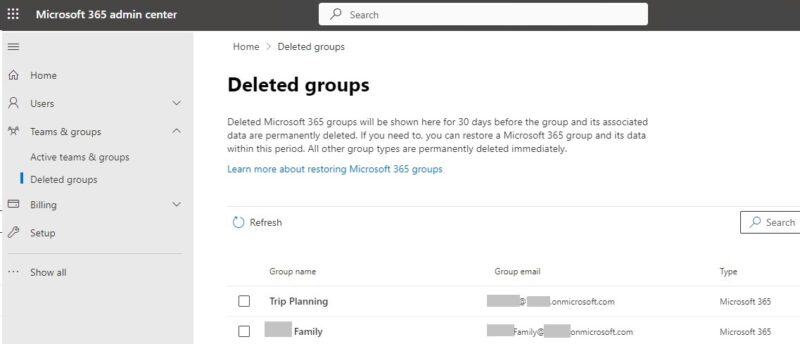
Once logged in, I found several active Azure accounts I had likely created for my family members and proceeded to purge them from the tenant. There also were two M365 Groups that contained said accounts as members:
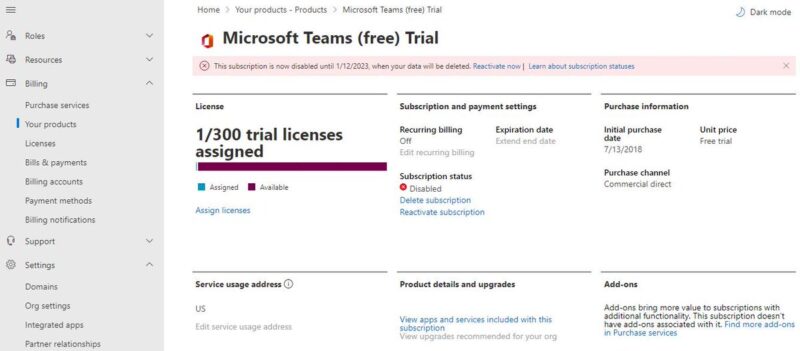
A Microsoft Teams trial was also on my account for 300 licenses. Aha! I now remembered having signed up for a free Microsoft Teams service to set up communication between family. Indeed, there was an “initial purchase date” of July 13, 2018, through the “Commercial direct” purchase channel. Note the “Commercial” part. So, THAT was how a business (commercial or work) subscription was associated with my personal domain!
Work vs Personal Accounts
Before Microsoft, Google, Apple, and other companies tied their products and services to a single account, software used to be purchased without requiring an email address. For instance, one could have gone to Fry’s Electronics, Best Buy, Circuit City, and other retail stores to buy physical copies of Microsoft Office, Sierra’s King’s Quest, WordPerfect, and Windows and install onto one or more computers (as per the license agreement) without the need for an email address. Even when software made the jump from physical media to digital, an email address was traditionally not required except for the retail store (like Amazon and eBay) it was bought from.
As time went on, companies learned that requiring an email address, such as a “Google Account”, was beneficial for them to learn about their customers. Collection of vast amounts of data became the new gold, and slowly, products and services were built around that account under the promise of “customized experiences” and license vaulting.
Products and services slowly required an email address to store licensing info with, app stores in particular.
The same was happening at the corporate enterprise with the use of Microsoft Azure Active Directory where employees were issued an account to log in to services with and to gain access to software like Office, Teams, SharePoint, and Exchange (Outlook) email. Some employees, however, used their work email address to sign up with personal Microsoft services and to log in to personal computers running Windows. When that employee left the company, he or she was faced with a sad reality: any personal app store purchases or services they bought under their work account could no longer be taken with them. On the flip side, employers had no idea what corporate data was left on a former employee’s personal computers while they were using their work email on those devices.
Microsoft later made the unpopular (but wise) decision to block work or school accounts from being used with personal products and services (ie. Microsoft 365 Personal) to segregate the two realms. This distinction allowed the employee to keep their personal things personal and their work or school data encapsulated within the responsible organization’s domain. Subsequently, Microsoft made it possible to use work and personal accounts side-by-side or, if permitted, the same email for both. The block was one of the reasons why Microsoft generally prevented an account associated with a business or school organization from being signed in to a personal computer or M365 subscription with.
Solution
How did I remove my personal domain from the Microsoft business/commercial/work association? First, I had to gain access to my domain’s Microsoft 365 Admin Center. If you do not remember your admin@tenant.onmicrosoft.com email address, contact Microsoft 365 Business Support. I had called the U.S. support line at (800) 936-4900.
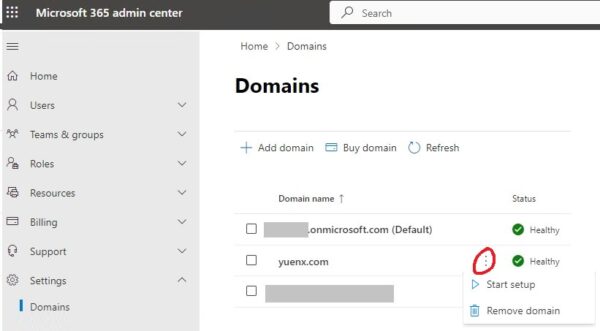
Navigate to Microsoft 365 Admin Center > Settings > Domains:
In the above screenshot, “yuenx.com” was listed as one of the domains associated with the commercial M365 tenant. Delete the domain you want to disassociate as a work or school organization by clicking on its three, vertical dots and choosing “Remove domain”. You should now be able to use your personal domain to sign into personal Windows and other Microsoft services after a short time.
Security
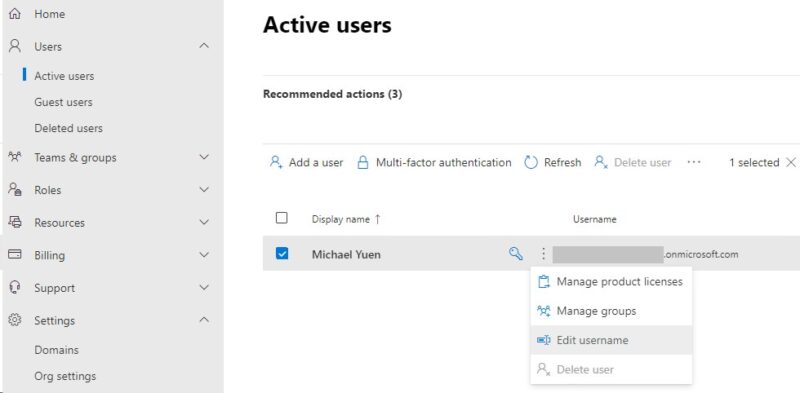
Since you are here, you should improve your Azure tenant’s security posture by renaming the default admin@tenant.onmicrosoft.com Global Administrator account to something obscure, like GeorgeMichaelBluth@tenant.onmicrosoft.com. The Global Administrator role can do ANYTHING with your Microsoft 365/Azure tenant and its details should be guarded with secrecy. Renaming it to something a malicious person cannot easily guess would make it more difficult for that person to gain access. To rename, go to Microsoft 365 Admin Center > Users > Active Users:
Select the Global Administrator’s account, click on its three, vertical dots, and “Edit username”. The change will log you off the admin center, and you may not be able to log in with the new username for a few minutes while Azure propagates the change throughout the Microsoft cloud datacenters.
Change the account’s password to something more secure, add an alternate email address for recovery, and update its Multi-factor authentication as needed. Review the recent sign-in activities.
References
- Microsoft
Related Posts
- Azure Active Directory
- Successful Logins from Unknown Users
- Audit Role Changes (ie. Global Administrator)