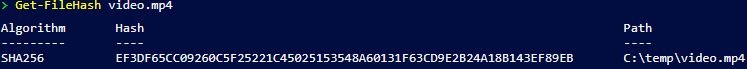Contents
Who Recorded The Meeting?
Recently, a sensitive, internal meeting was held within Microsoft Teams, and someone had accidentally recorded it. The organizer was extremely unhappy when nobody admitted to it, particularly since any attendee was able to download a copy of the recording. An urgent request to the Office 365 and Information Security teams was put out to investigate:
- Who recorded the meeting?
- Who downloaded a copy of the recording?
It was imperative that any copies of the meeting were located and destroyed. How did we go about in doing so?
Where Do Recorded Meetings Go?
Let us first discuss where Teams meeting recordings go. (Refer to this document: Microsoft Teams Cloud Recording)
According to Microsoft, if a user has a valid Microsoft Stream license within Office 365/Microsoft 365 (among other prerequisites), the recording would be uploaded to the Microsoft Stream cloud and be available for distribution. That user or a person with sufficient rights can then go there to share and delete said media.
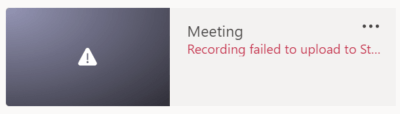
Recording failed to upload to Stream?
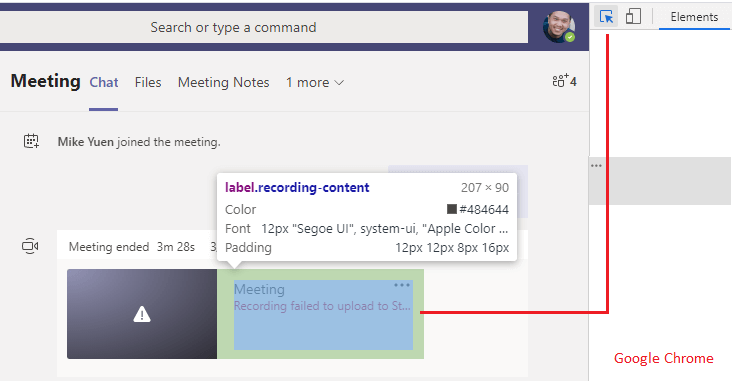
What happens when a recording failed to upload to the Stream cloud, as shown below?
The issue may occur if the user does not have a Microsoft Stream license assigned to his or her account. So, where exactly is the recording saved then? After searching for more than two hours, my colleague, Todd Nelson [Disclaimer: received permission to include his name], and I were unfortunately not able to find the answer but will update this post when or if we do. Meanwhile, a support case with Microsoft was opened.
If I remember correctly, the recording would no longer be available after 6 days.
Who Downloaded The Recording?
Next on the list was to determine who had a copy of the meeting. We noticed that you could download by clicking the three dots in the upper-right corner of the recording. The resulting file is stored as “video.mp4” by default. You could now perform an enterprise-wide search for any file matching the “video.mp4” name, but what if it was named something else? Without a tool like Carbon Black or CrowdStrike Falcon, locating files across the entire organization could be a frustrating task.
We also found that anybody who downloaded the “video.mp4” file from the meeting had the same file hash, no matter what it was named.
A hash is an irreversible, calculated value of a file to uniquely identify it — any change to the file would result in a different hash. A hash is used to validate that a file has not been modified
You can obtain the hash of a file in various ways, but the quickest method is through PowerShell on a Windows system:
- Get-FileHash video.mp4
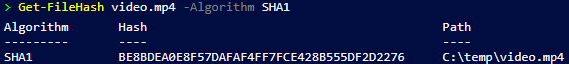
- Get-FileHash video.mp4 -Algorithm SHA1
The first command will obtain the hash with the default SHA256 algorithm:
The second command shows the SHA1 hash:
With the hash value for video.mp4 (“EF3DF65CC09260C5F25221C45025153548A60131F63CD9E2B24A18B143EF89EB“) in hand, we scanned the attendees’ computers for it using PowerShell, Compliance and Forensics tools, and other methods. Below is a crude script to recursively look for the file hash on a remote computer’s “c:\users\username\downloads” folder:
# Obtain file's hash $Hash = (Get-FileHash c:\temp\video.mp4).hash Write-Host "Hash: $Hash" -f Yellow # Computer and User to check $Computer = "TestComputer"; $User = "TestUser" $ComputerPath = "users\$User\downloads"; $ScanPath = "\\$Computer\c$\$ComputerPath" # Scan target computer and path for any file matching the hash Get-ChildItem $ScanPath -Recurse | Get-FileHash | Where hash -eq $Hash
The above script will display any file matching the hash:
With the hash, you can also utilize your Data Loss Prevention tools to see if anybody may have emailed the file out, for example.
Who Made The Recording?
None of the attendees raised their hand when asked, “Who is recording this meeting?” Naturally, the organizers came to the Office 365 engineers to find that answer. Did we find out? Not immediately. Recall that the recording failed to upload to the Microsoft Stream cloud, and so we could not use any of the Office 365 compliance tools to investigate.
My colleague, Todd Nelson, opened a case with Microsoft, and here was the solution:
- Go to Teams from a browser: https://teams.microsoft.com
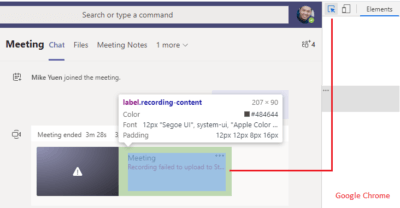
- Look for the recording:

- Right-click the “Meeting” word and select:
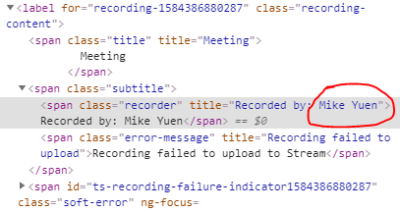
- From the resulting inspection, locate the <span class=”title” title=”Meeting“> tag
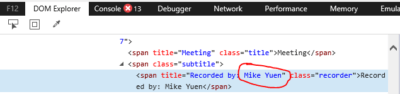
- Expand the <span class=”subtitle“> class, and within, you will find “Recorded by:”
- Shown will be the name of the person who initiated the recording
In this article, we went over:
- Why a meeting recording may have failed to upload to the Microsoft Stream cloud
- How we have not yet found where failed meetings are saved locally
- How to obtain the file hash for the downloaded video
- How to find any computer who may have a copy of the recording using the file hash
- Who recorded the meeting
Be safe! Be vigilant!